Types of Malware and Vulnerabilities – There are many types of malware and vulnerabilities. And we will list the most common ones and how to protect ourselves against them.
When we browse the Internet. We expose to a series of risks, which can jeopardize the security of our devices and cause our data to end up in the wrong hands.
Today’s society, where we are permanently connect. Is the ideal terrain for cybercriminals to act.
There is an increasing number of potential victims of their attacks, and the fact that we now use our devices to do almost anything only increases the risk.
Table of Contents
Definition
Malware comes from the English words “malicious software” or malicious software.
Its goal is to infiltrate and damage a computer or device without the consent of its owner.
Malware is the generic category, which encompasses all other computer threats, including viruses.
Malware Propagation Mechanisms
Computer viruses and other forms of malware can access our devices in different ways:
We may receive a message with attached files that are infected.
Downloads
It is essential to fully understand the source of a download link before executing it.
Messaging Apps
As in the case of email, we can receive malicious links or attachments through applications such as WhatsApp, Facebook Messenger or an SMS.
Outdated Software
If you don’t have the software on your device up to date, the risk of it becoming infected or suffering from a cyber attack will be higher.
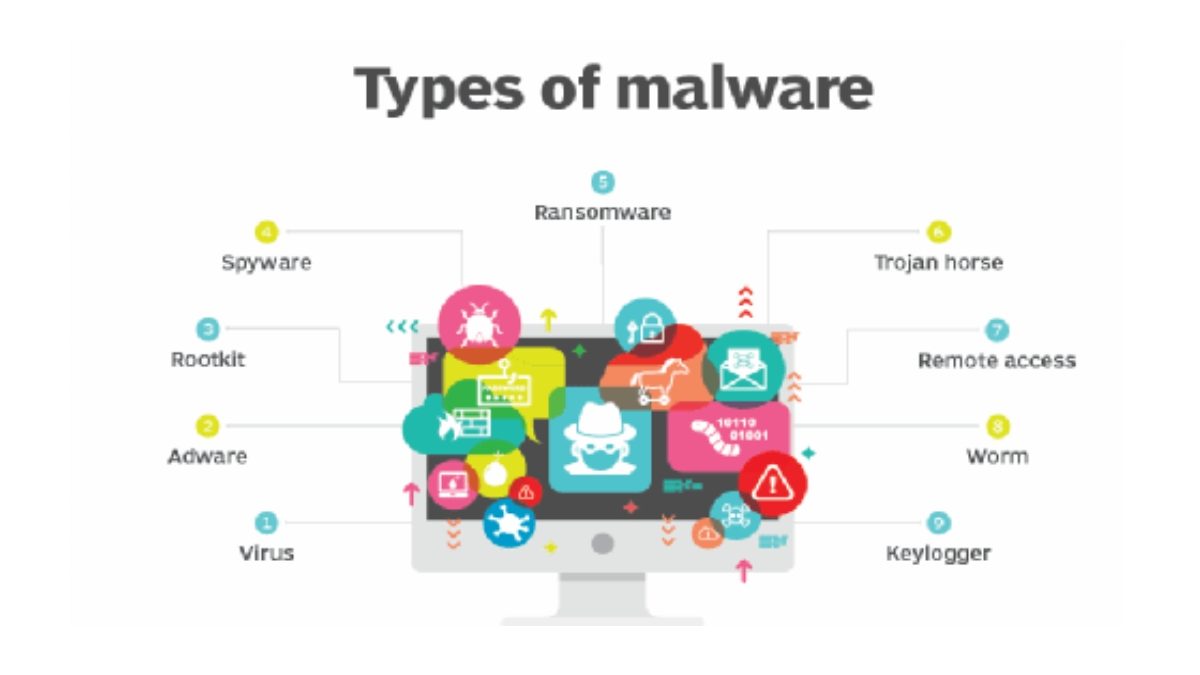
Types of Malware and Vulnerabilities
Within the concept of malware would be computer viruses and other types of vulnerabilities, whose image we will try to clarify below.
Computer Virus
A computer virus can define as harmful software that has the objective of altering the normal functioning of a computer device.
It enters the device without the user’s permission and knowledge and mainly has malicious purposes.
They are characterize in that they need user intervention to be executed.
Its effects can vary, from causing our devices to malfunction or exaggeratedly slow performance to the destruction or corruption of files.
Computer Worms
This malware resides in the device’s memory and replicates itself without user intervention.
They use computer networks to spread over the Internet, sending themselves to your contact list and trying to infect your computers.
They usually consume system resources and affect performance, but they can also steal or delete files.
Logic or time Bombs
They are activated when a specific event occurs, such as on a date or by a key combination.
If that circumstance does not occur, they remain hidden.
Spyware
They instal on your computer without you realizing it, and their purpose is to spy on what you do, to obtain specific information, which can end up in the hands of cybercriminals.
This category would be the so-called keylogger, or key logger, which monitors the keys we press to find personal passwords or other relevant information.
Ransomware
Moreover. A hacker or cybercriminal takes control of your computer equipment and requests payment of money from the device’s owner to release it.
They encrypt your data and, if you don’t pay, threaten you with publishing certain sensitive information on the Internet or destroying all your information.
Adware
It usually is not considered malware because its ultimate purpose is not to harm.
It displays unwanted advertisements in the form of pop-ups while browsing the Internet or as advertisements that accompany free software.
Sometimes, they can track our computers and offer us advertising based on the web pages we visit or our searches.
These are the most well-known types of malware, but there are wide more varieties, and new threats appear on our devices daily.
Tips to Protect Yourself Against Malware
There are a series of basic guidelines that can help us protect ourselves from malware and other computer threats:
- It is highly recommend always to have your device updated to the latest operating system version, as well as install a good antivirus.
- Try to download files only from known and safe sites. Avoid downloading or opening links from suspicious emails or websites.
- Also, do not download pirated software; you risk it containing malware.
- Avoid browsing web pages that are not secure.
- Be careful when using other people’s flash drives or external memories. They may infect with some computer virus.
- Do not click on any ads or pop-up messages.
- Being guided by common sense and caution is the best advice in these cases.